
What is contrast-color() in CSS? The contrast-color() function, part of CSS Color Level 5, automatically selects a color that contrasts well with a reference color, usually the background. Its main purpose is to...

What is contrast-color() in CSS? The contrast-color() function, part of CSS Color Level 5, automatically selects a color that contrasts well with a reference color, usually the background. Its main purpose is to...

A new Windows 11 update (24H2 KB5063878) is reportedly causing serious SSD and HDD issues for users worldwide. If you have recently installed this update, your storage drives may be at risk. 🔎...

Since late 2023, Google Gemini has emerged as one of Google’s most ambitious artificial intelligence projects. Designed to compete with OpenAI’s ChatGPT, this multimodal model promises to transform the way we work, learn,...

In modern front-end development, managing HTTP requests is becoming increasingly complex. Between loading states, error handling, caching, synchronization, and interdependent requests, a simple fetch or even axios is often no longer sufficient. This...

When it comes to relational databases (SQL), the term ACID comes up often. Behind this acronym lies a set of essential guarantees that ensure data reliability, consistency, and safety. Whether you’re a developer,...
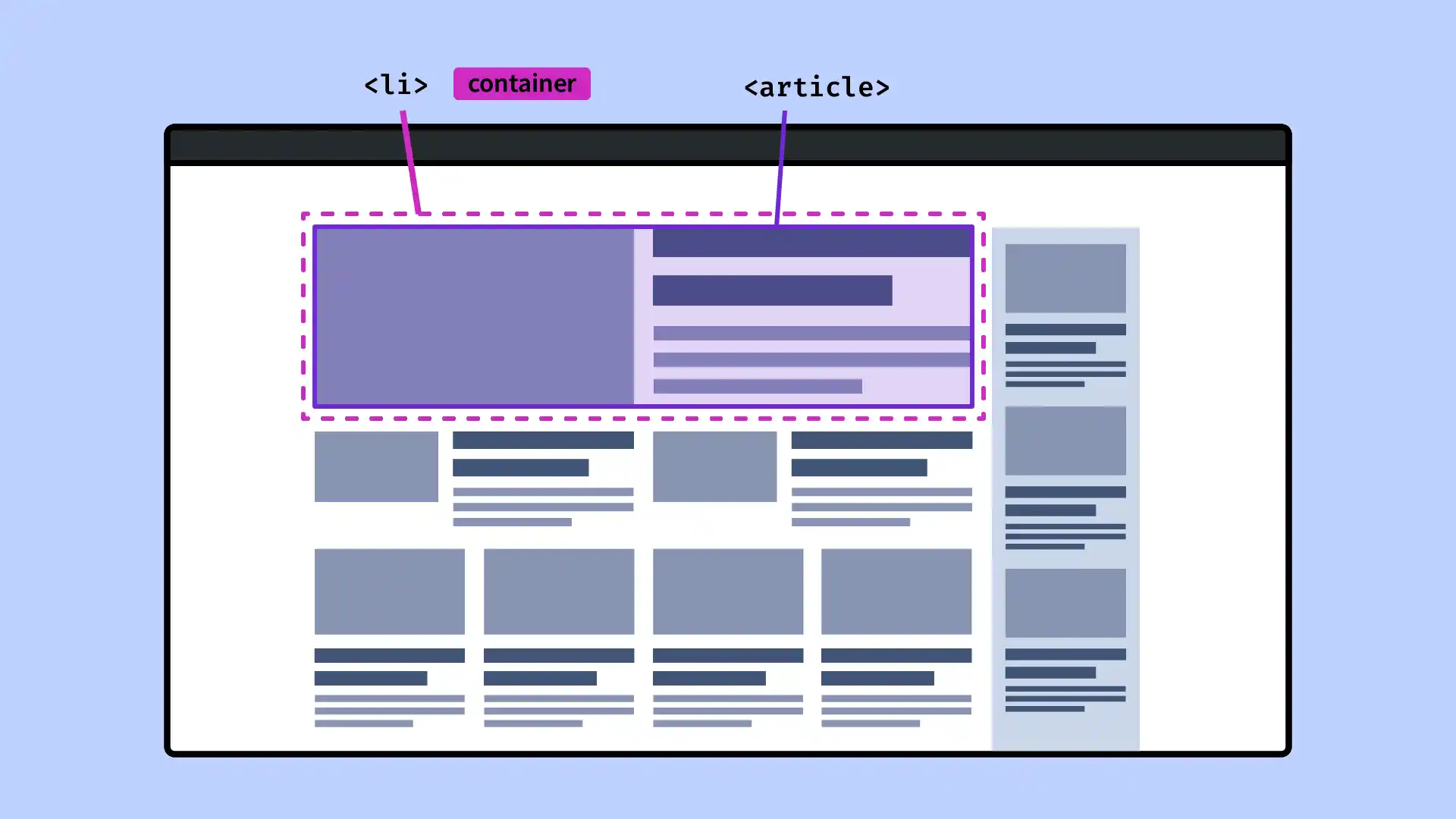
When we think of responsive design, the first thing that comes to mind is @media. But with the arrival of Container Queries, a new era begins: one where components can adapt their style...

The major concept of the XSS attack is to utilize certain vulnerabilities in web applications, allowing attackers to inject malicious scripts into the user’s browser. These injected scripts can steal sensitive information, hijack...

In the world of web development, understanding Web Storage is essential for managing client-side data efficiently. Among the various options available, Session Storage, Local Storage, Cookies, and IndexedDB each offer unique benefits. While...

The Domain Name System (DNS) is a cornerstone of Internet infrastructure. It translates human-readable domain names (such as example.com) into IP addresses, enabling machines to locate online resources. This article explores the fundamental...

Protocol Buffers, commonly known as Protobuf, is a powerful data serialization tool developed by Google. It provides a flexible and efficient solution for transferring information between systems. Protobuf is language- and platform-independent, making...



Simple App : a blog simplifying development and cybersecurity. Accessible guides and tips to boost your skills in tech and security



© 2024 Created by Simple App