In today’s digital age, the need for secure communication is more critical than ever. Encryption and digital signature play a vital role in enhancing security and ensuring the integrity of electronic messages. These technologies provide the foundation for confidentiality, authenticity, and reliability in digital interactions. Here, we explore how encryption and signatures work, their processes, and their practical applications in maintaining secure communication.
What Is Encryption?
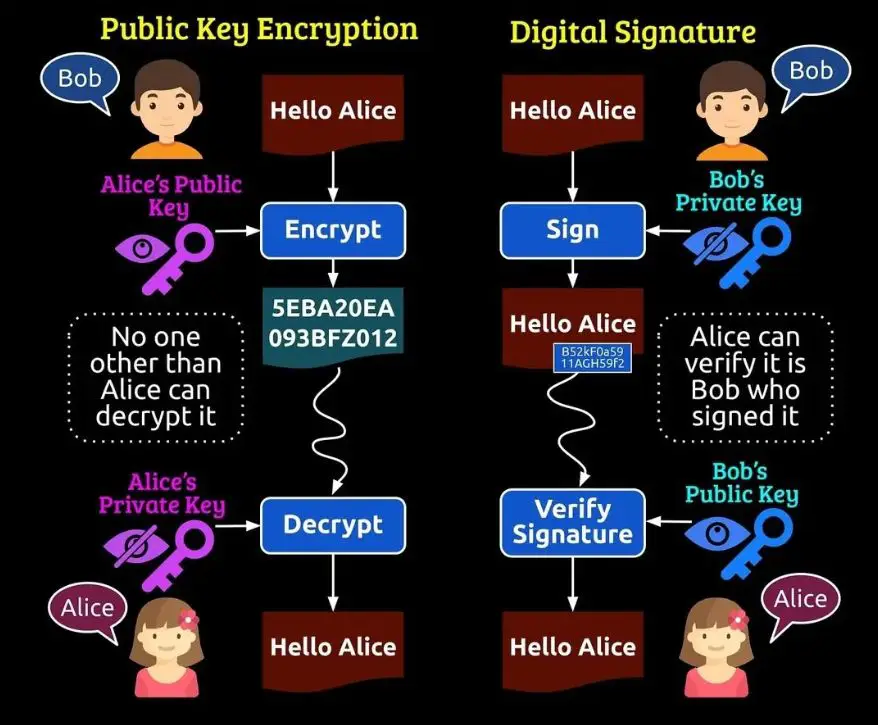
Encryption is the process of transforming data into an unreadable format to protect it from unauthorized access. It ensures the confidentiality of the message, allowing only the intended recipient to read its content.
How Does Encryption Work?
- Encryption by the Sender:
- The sender encrypts the message using the recipient’s public key. This key is publicly available and ensures that only the intended recipient can decrypt the message.
- Decryption by the Recipient:
- The recipient, using their private key, decrypts the message and accesses its content. The private key is kept confidential and is unique to the recipient.
Use Case: Protecting Confidential Information
Encryption plays a crucial role in safeguarding sensitive information. For example, it protects confidential business emails or financial data during transmission, ensuring that even if someone intercepts the message, unauthorized parties cannot access its content .
What Is a Digital Signature?
A digital signature uses cryptographic mechanisms to verify the authenticity and integrity of a message. It assures the recipient that the sender created the message and that it remains unaltered during transmission.
How Does a Digital Signature Work?
- Creating the Digital Signature:
- The sender calculates a digital fingerprint (hash) of the message.
- This hash is then encrypted using the sender’s private key, resulting in a digital signature.
- Verifying the Digital Signature:
- The recipient uses the sender’s public key to decrypt the signature and retrieve the hash.
- The recipient calculates the hash of the received message and compares it with the decrypted hash. If they match, the message is verified as authentic and unaltered.
Use Case: Ensuring Authenticity and Integrity
Digital signatures find applications in areas such as e-commerce, software distribution, and legal documentation. For instance, when an electronic contract is signed, the technology verifies the identity of the signer and ensures the document’s integrity, confirming it has not been altered .
Key Differences Between Encryption and Digital Signatures
| Aspect | Encryption | Digital Signature |
|---|---|---|
| Purpose | Ensures confidentiality of the message | Ensures authenticity and integrity of the message |
| Key Used for Process | Sender uses recipient’s public key for encryption; recipient uses their private key for decryption | Sender uses their private key to create the signature; recipient uses sender’s public key for verification |
| Use Case | Prevents unauthorized access to message content | Verifies sender’s identity and message integrity |
Conclusion
Encryption and digital signatures are indispensable tools in modern cybersecurity. Understanding The Difference Between Encryption And Digital Signature is crucial, as encryption safeguards sensitive information by preventing unauthorized access, while digital signatures ensure the authenticity and integrity of messages. By integrating these technologies and recognizing The Difference Between Encryption And Digital Signature, organizations and individuals can enhance security and establish trustworthy communication in an increasingly interconnected world


