Cybersecurity is an essential field focused on protecting information systems from various threats. It is generally divided into two main...

Cybersecurity is an essential field focused on protecting information systems from various threats. It is generally divided into two main...

If you’re building a modern web app with React, adding smooth UI animations can greatly enhance the user experience. Framer Motion is a powerful animation library built for React developers, offering a simple...

Python is a favorite language among ethical hackers and cybersecurity experts due to its simplicity and powerful libraries. In this article, we’ll explore some of the most useful Python libraries for hacking and...

In modern front-end development, managing HTTP requests is becoming increasingly complex. Between loading states, error handling, caching, synchronization, and interdependent requests, a simple fetch or even axios is often no longer sufficient. This...

When creating a responsive web interface—especially for mobile—you often run into a frustrating issue: the viewport height (100vh) doesn’t always behave as expected. The address bar disappears, the keyboard pushes everything upward… Sound...
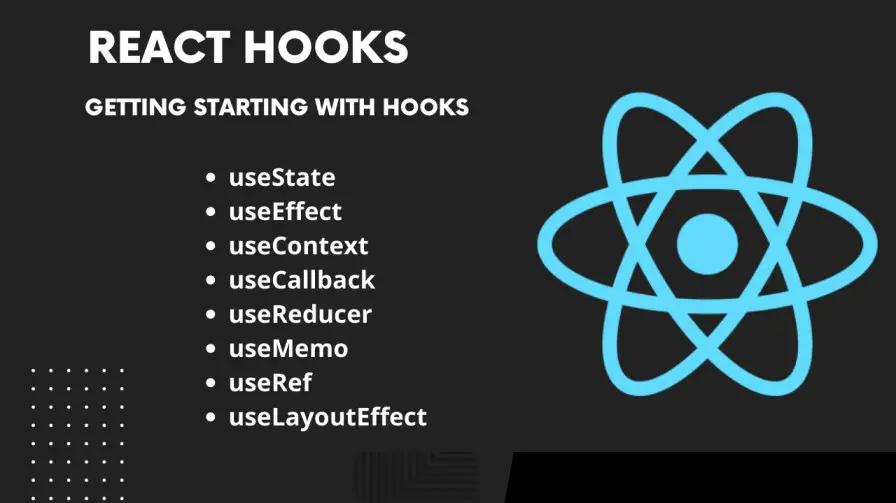
Since React 16.8, Hooks have transformed the way we write components. They allow you to use state, lifecycle methods, and other advanced features without writing class components. Here’s a complete guide to understanding...
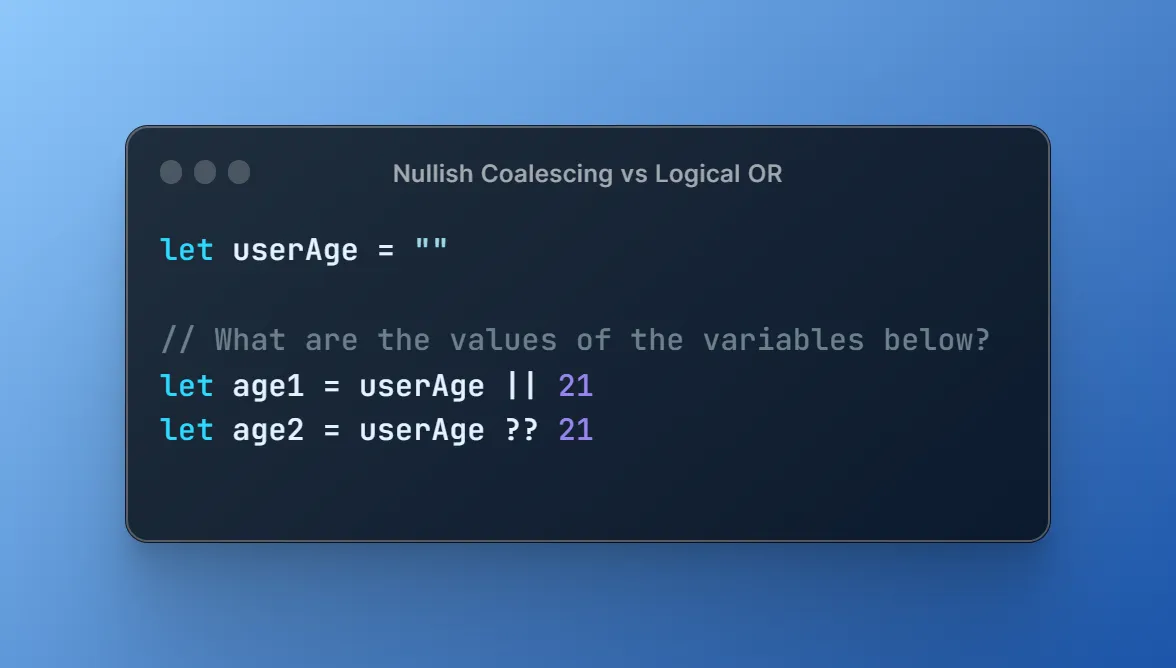
JavaScript keeps evolving to offer developers more powerful and readable tools. One of the most useful recent additions is the Nullish Coalescing Operator (??), introduced in ES2020. This operator may seem subtle at...

State management in React apps can often become a major headache. Between Redux, Recoil, Jotai, or the Context API, choosing the right solution can be overwhelming. But one tool has recently been gaining...

When it comes to relational databases (SQL), the term ACID comes up often. Behind this acronym lies a set of essential guarantees that ensure data reliability, consistency, and safety. Whether you’re a developer,...
When building applications with React, state management quickly becomes a challenge as multiple components need to share the same data. This is where React Context comes in. In this article, you will learn:...
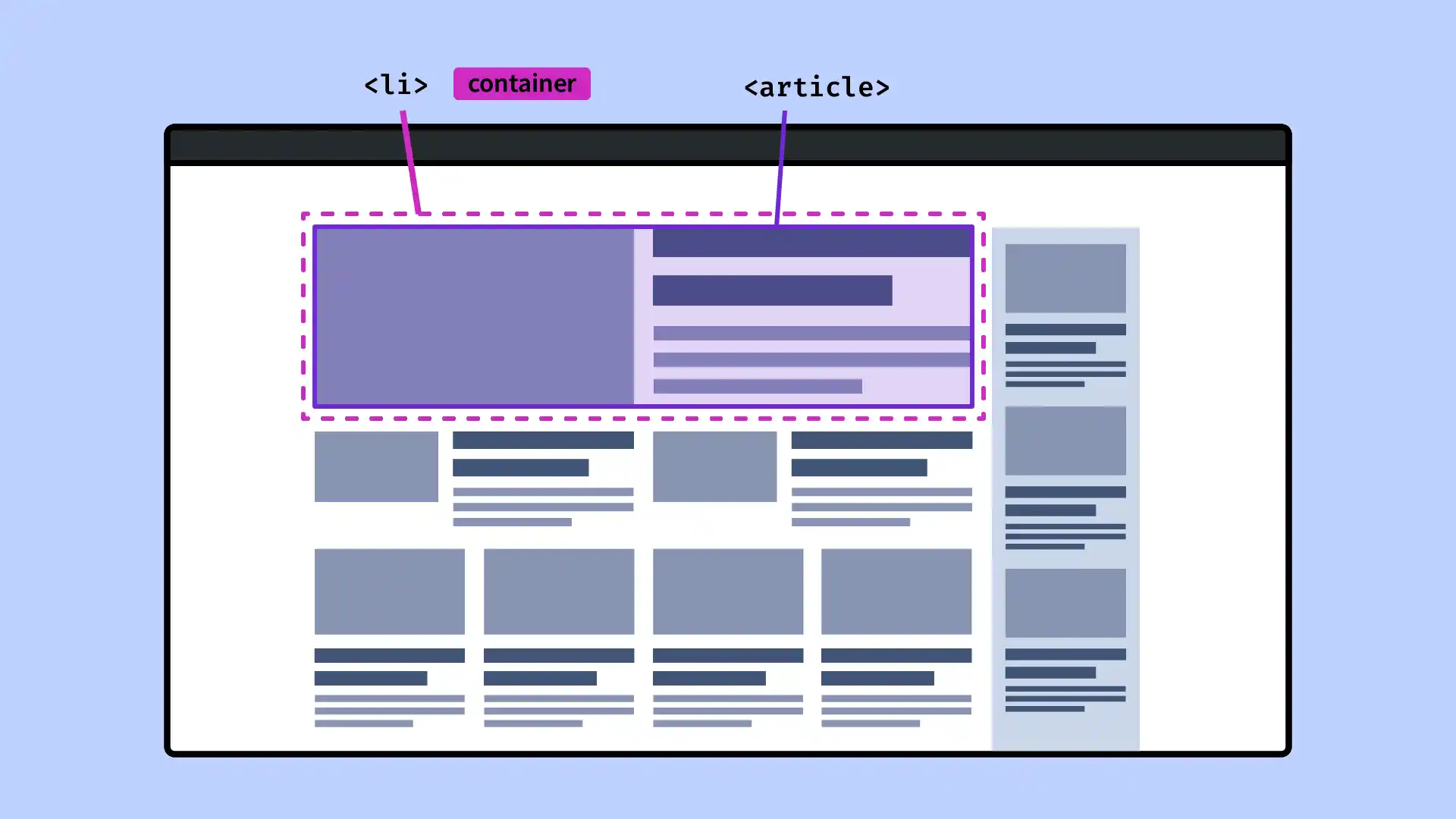
When we think of responsive design, the first thing that comes to mind is @media. But with the arrival of Container Queries, a new era begins: one where components can adapt their style...

Simple App : a blog simplifying development and cybersecurity. Accessible guides and tips to boost your skills in tech and security

© 2024 Created by Simple App